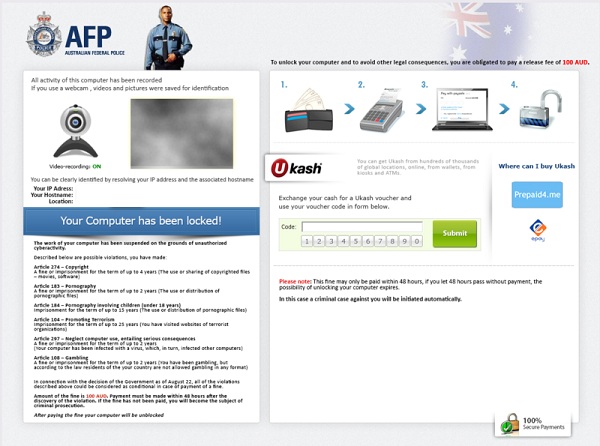
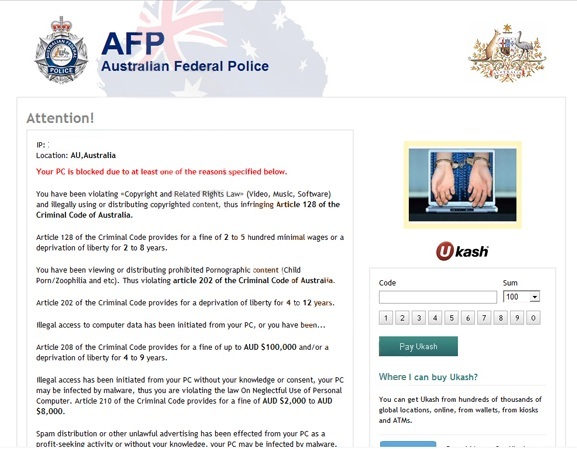
The ‘Ukash Ransom‘ virus also known as the Australian Federal Police (AFP) virus is a computer virus which will display a bogus notification and pretends to be from the Australian Federal Police. It states that your computer has been blocked due to it being involved with the distribution of inappropriate content. The virus will display a lock screen and ask you to pay money (i.e. a non-existing fine).
Like many other ransomware infections spread in the wild such as FBI Moneypak virus, this AFP ransomware also exploits system vulnerabilities to infect computer system. Once settled, the AFP ransomware will totally lock you out of your computer and applications, so whenever you’ll try to log on into your Windows operation system (or sometimes even in Windows Safe Mode), it will display a lock screen asking you to pay a fake fine of AUD $ 100, or AUD $200, etc depending on its version, in the form of a Ukash or Paysafecard code.
Note that this virus is not cryptoware; it does not encrypt files on your computer offering to decrypt them only if the user pays a ransom. That said, this virus comes in a number of variations and may well be bundled with other malicious programs. The AFP ransomware virus is quite successful in infecting computers. It could easily be modified to carry a different payload.
Furthermore, to make this alert seem more authentic, this virus also has the ability to access your installed webcam where the bogus Australian Federal Police notification shows what is happening in the room. If your computer is infected with Australian Federal Police virus, then you are seeing any of the below notifications:
Example #1
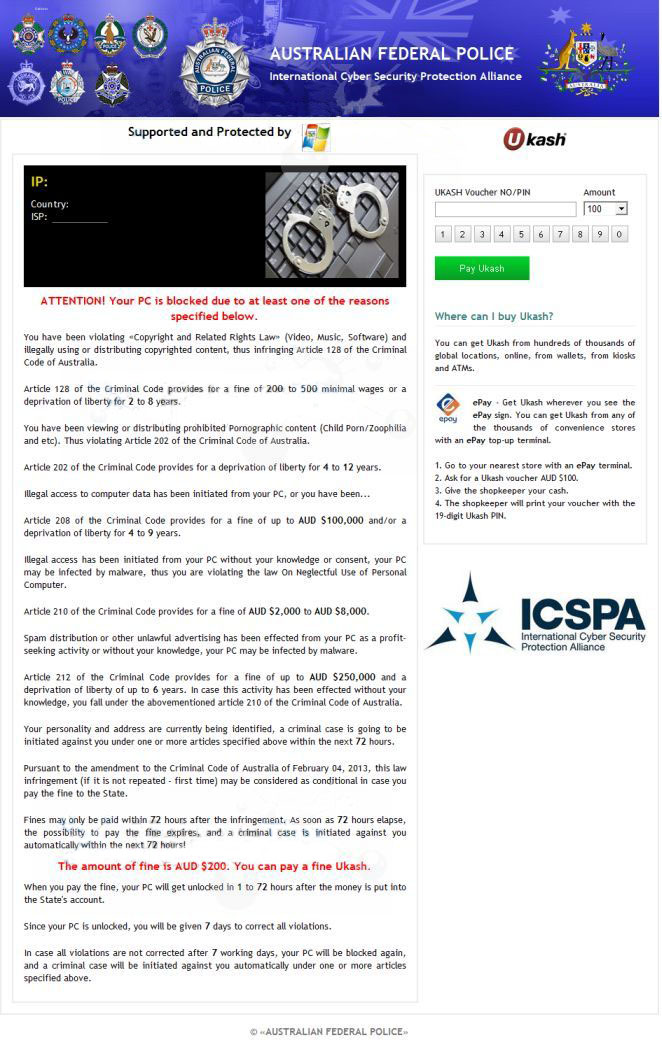
The Australian Federal Police Ransom is a scam. You should ignore any alert or suggestion to transfer money or provide personal information. You should attempt to remove this ransomware virus from your computer. Under no circumstance should you transfer money or provide personal details as this does nothing to unblock your computer and could lead to identity theft.
Basic removal instructions
The process to remove this virus involves the following steps:
- Reboot your computer into Safe Mode with Command Prompt:
- Windows 7 Safe mode
- Windows 8 Safe mode
- System Restore.
- Anti malware scan.
Safe Mode with Command Prompt
Reboot your computer into Safe Mode with Command Prompt. Please use the instructions for Windows 7 or Windows 8:
Windows 7 Safe mode
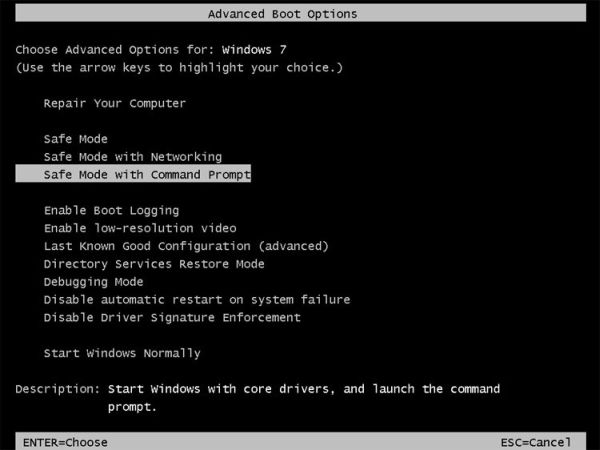
To access Safe Mode with Command Prompt, turn your computer off and then back on and immediately when you see anything on the screen, start tapping the F8 key on your keyboard.

Windows 8 Safe mode
If you are using Windows 8, the trick is to hold the Shift button and gently tap the F8 key repeatedly immediately after restarting the computer. By doing this it will take you to the new recovery mode where you can access advanced repair options.
Alternatively, you can hold the power button for 10 seconds while the computer is starting up to force an immediate shutdown; when you restart the computer next, it will automatically boot into recovery mode to attempt and diagnose boot problems.
On the next screen, you will need to click on the Troubleshoot option, then select Advanced Options and select Windows Startup Settings. Click on the Restart button, and you should now be able to see the Advanced Boot Options screen. Using the arrow keys on your keyboard, select Safe Mode with Command Prompt and press Enter on your keyboard.
System Restore
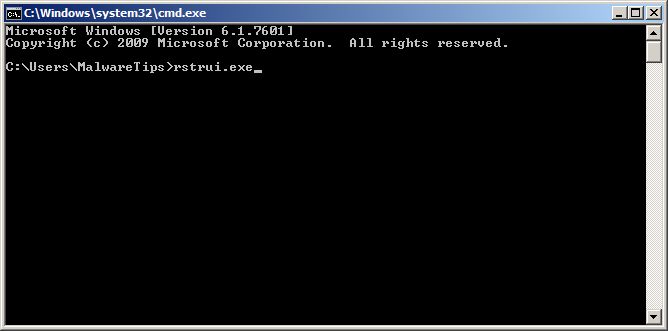
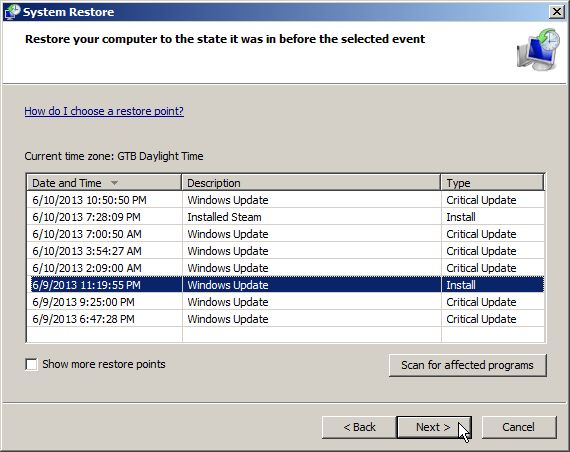
When you have successfully booted into Safe Mode with Command Prompt, at the command prompt, type rstrui.exe, and then press ENTER.
System Restore should start, and you will display also a list of restore points. Try using a restore point created just before the date and time the Australian Federal Police lock screen virus has infected your computer.
When System Restore has completed its task, start your computer in Windows regular mode. The virus lock screen should no longer appear.
Anti malware scan
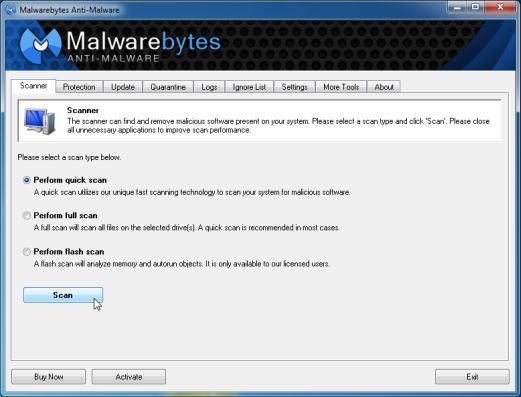
Download Malwarebytes Anti-Malware Free.
Follow the installation prompts and start the program.
Malwarebytes’ Anti-Malware will now start scanning your computer for malicious software.
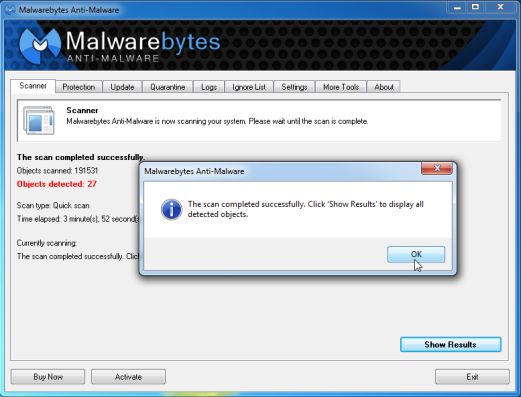
When the Malwarebytes Anti-Malware scan has finished, click on the Show Results button.
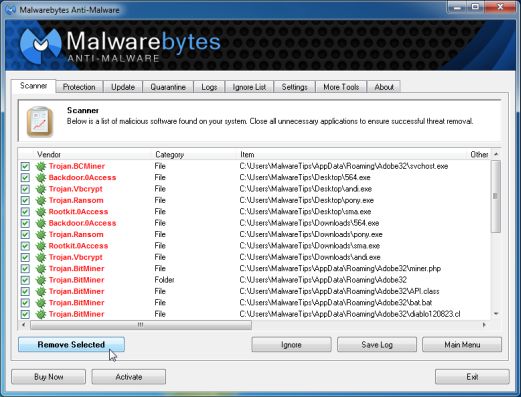
You will now be presented with a screen showing you the computer infections that Malwarebytes Anti-Malware has detected. Make sure that everything is Checked (ticked), then click on the Remove Selected button.
You could run additional virus removal utilities if you want to be absolutely certain all malicious software has been removed.
Advanced removal instructions
If the virus is also present when you access Windows Safe mode, removal will be more difficult. You would need to use software like Anvi Rescue Disk to regain access to your computer.
Detailed instructions can be found here:
http://www.dotfab.com/resources/how-to-remove-australian-federal-police-afp-ukash-virus-ransomware-removal-guide/
Conclusion
The ‘Ukash virus’ or Australian Federal Police (AFP) virus is successful in bypassing Windows security. Depending on whether or not you are able to use Windows Safe mode it may be fairly straightforward or rather difficult to remove.
Always be careful when opening email attachments from an untrusted source or when visiting web sites that could serve infected files for download or hidden in malicious advertisements.